It’s important to note that a vulnerability scan is not a pentest. Automation isn’t a bad thing, it’s actually extremely useful as a pentester, but it’s important to also recognize that there is a distinct difference between the two.
A vulnerability scanner is programmed to discover vulnerabilities in applications and systems — they will find what they are programmed to find but will miss everything they are not. Manual pentesting layers human expertise on top of these tools. Many pentesters use a hybrid approach to leverage automation where appropriate and then manually dig deeper for more advance vulnerabilities.
You should not rely solely on automated vulnerability assessments. Manual analysis and applying human expertise is key to make more educated and real guesses.
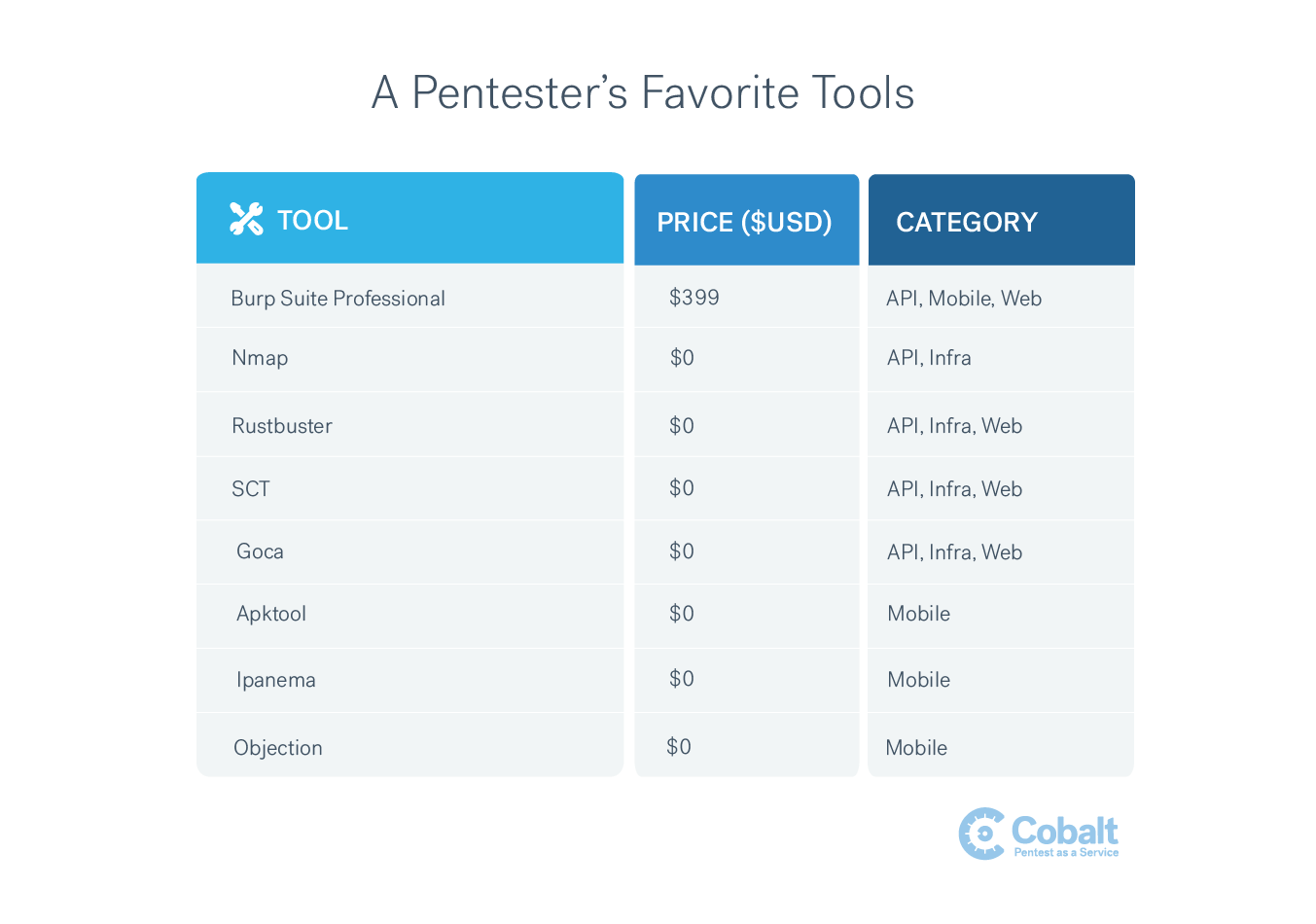
Every pentester has his/her favorite toolset. In this blog entry, I will share a list of my favorite tools that you can leverage to help automate some of your work so that you can dive into the more interesting things that a scanner can’t find:
-
Burp Suite Professional: Probably the most common tool among penetration testers. Burp Suite is an integrated platform for performing security testing on web applications. It covers over 100 generic vulnerabilities, such as SQL injection and XSS. Burp allows you to see every request performed by your browser and furthermore, it allows you to edit and repeat them. The main difference between the Community Edition and the Professional one is the web vulnerability scanner, a really useful tool which helps you identifying potential vulnerabilities in a short amount of time.
-
Nmap: Another well known scanning tool in the IT community; Nmap, is a free and open-source network scanner that is used to discover hosts and services on a computer network by sending packets and analyzing the responses. In my opinion, it is the cornerstone of every infrastructure pentest. With nmap, a pentester can see which ports are open which helps give us a general roadmap for trying to get into an internal network from the Internet.
-
Rustbuster: This tool is relatively new to my toolkit! The author released it about four months ago, and I’ve been testing it out over the past few weeks. It’s a comprehensive web fuzzer and content discovery tool. There are many directory brute forcers out there (gobuster, dirb, dirble or dirsearch to mention some of them), but I really like this one and is the one I’m using at the moment. Keep in mind that the important thing when performing directory brute-forcing is the wordlist in use rather than the tool itself.
-
SCT: This tool helps me during the initial phase of the web application assessment. It helps me identify which security headers are in place or which cookie attributes are set.
-
Goca: I use this tool mostly during infrastructure pentest and occasionally for web application testing. This scanner allows you to look for different documents in the network from a given domain and then checks those documents metadata. It’s amazing how much information is possible to extract (authors of documents, emails, etc). From there, the next step will be to cross-check those users with password leakage databases and eventually, get valid credentials.
-
Apktool: A tool that can be used to decompile or reverse engineer Android applications during mobile assessments for static analysis. After decompilation, a little bit of *grepping *and you are good to go.
-
Ipanema: The unknown of the list. I use ipanema to analyze, statically, iOS applications. It gives you all the information you can get from other tools, but in a short amount of time. The good point is that this is a Golang program, hence it is a single binary. No need to deploy docker containers or install hundreds of requirements.
-
Objection: Runtime mobile exploration powered by Frida. This tool helps out a lot during mobile assessments. It helps with bypassing the SSL pinning to see clear-text communications between the application and the server, getting information from memory, looking for credentials being saved locally by the application or dumping the iOS keychain along many other things.
This is just my short list, there are many other tools I leverage depending on the situation and how the test is going, but these are my basic go-to’s, the ones I am carry in my toolbox.
Is there an essential tool you think I am missing? Let me know!
Learn more about Cobalt’s amazing pentester community or if interested, apply to join the Cobalt Core here.